What Does it Mean to Be a Security personnel?
What Does it Mean to Be a Security Guard?
When it involves protection, among the major worries is what is things safety and security? This is a really intricate subject that covers every one of the various protection concerns that take place in a building or any kind of other structure. These concerns vary from simple to very complex as well as entail any kind of number of different people as well as or items.
When Dutch Crowd Security think about the various sorts of security guard tasks that can be covered, it is easy to see why item protection is such a complicated as well as wide subject. When the guard is dealing with the within a building, there are a lot of various things that can take place. For instance, it can cover the reality that the guard needs to examine to ensure that no one is in a restricted area or that a secured door is closed in front of them.
When you take into consideration the guard servicing the outside of a structure, it is very easy to see why they are in the position of being able to keep an eye out for people and also items that can take place. One example is the security guard operating in a stockroom and examining to make sure that there are no employees or clients around. If there is, the guard will certainly need to make sure that they are working securely or that they are aware of what they are doing.
When you think about what things security guard activities actually involve, you can see why there are many different kinds of points that a security personnel can be called upon to do. These various types consist of the following:
A standard thing to see concerning any type of security guard activity is that the security guard is going to require to be trained in order to be able to execute it well. The type of training that a guard has to go through is mosting likely to depend upon just how advanced their task is mosting likely to be. For instance, some guards just need to go through standard training, while others require to undergo more advanced training to perform their work in the very best feasible way. It can likewise depend upon what type of work the guard is carrying out.
It is also really vital to ensure that the security guard is a great communicator. The much more that a guard is able to communicate with the people they are mosting likely to be collaborating with, the most likely that they are going to have the ability to execute their task appropriately and also effectively.
The degree of security that a security personnel activity is going to have is mosting likely to be one of the other significant points to check out. This is a huge worry due to the fact that a guard can do a great deal of different things that will increase the protection of a structure or any type of provided day, yet if the protection in that building is low sufficient, then it will certainly not be able to effectively secure the people inside of the building. One example of this is that if a high level security is absent, after that an intruder might have the ability to survive the doors, enter into the building and take whatever he desires.
A great deal of the guard tasks that can be done include a guard going to particular locations inside a structure to ensure that the guards outside are working. This implies that they will certainly have the ability to inspect the safety and security of the structure as well as ensure that the guards on the inside are refraining anything that is going to make them vulnerable.
The kinds of items that a security guard can be contacted to deal with include but are not restricted to:
There are many different sorts of security guard jobs that a security guard can do. All you need to do is look at things that are involved in each one of the different kinds of security guard work and then think about what it is that you are searching for in a security guard to be able to do in order to ensure that you are working with someone that will be able to do the job right the first time that you do it.
Security guards are going to be one of the most vital people that you are mosting likely to find helping a firm. and you are mosting likely to intend to ensure that you are employing a person that will have the ability to get the job done right.

Best Resume Formats For 2020 [3+ Professional Templates] Guard
What Are The Various Types Of It Security?
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Specialist Driving Ability
Employing a fully trained licensed security guard to do a temperature check on any individuals entering your establishment is essential in your duty to aid guard your neighborhood. ondersteuning van beveiligingsbedrijf suggest these services for all dining establishments, retailers, markets, business as well as domestic structures.
Managers and managers need to recognize that their habits affects every person around them. Upper management requires to hold these individuals responsible to safety, and also not look the other way as long as production objectives are being met. If you intend to develop a solid safety and security society at your company, you have to begin with your leaders. Your supervisors and also supervisors need to set the instance for everybody else. They demonstrate the version for safe habits that everyone else will comply with.
Whizrt: Substitute Intelligent Cybersecurity Red Group
Sweetheart Dietl & Associates is a leading private investigation as well as security company headquartered in New York City with workplaces in New Jersey, Florida, as well as Beijing, China. The bottom line is to never ever compromise on the top quality of a bodyguard. Beau Dietl & Associates has expert bodyguards with all of these qualities, so you recognize you as well as your possessions will certainly remain in great hands. If you would certainly like to find out more concerning our security services, contact us.
Add Your Call Info Properly
Customer support abilities are traits and methods that assist you deal with consumer requirements to develop a favorable experience. As a whole, customer care skills depend heavily on problem-solving and also interaction. Customer support is usually thought about a "soft ability," consisting of traits like energetic listening and also analysis both spoken and also nonverbal hints.
Consider what personal skills or qualities aided you meet that landmark. Raising health and safety recognition in all levels within the company. A security perception study can assist you evaluate your company's safety culture to figure out locations for enhancement. Managers should be held accountable to lead by example every day.
What are the duties and responsibilities of a security guard?
Data security refers to the process of protecting data from unauthorized access and data corruption throughout its lifecycle. Data security includes data encryption, tokenization, and key management practices that protect data across all applications and platforms.
- Instead, you will need to write code like revealed over for your individual domain objects.
- It deserves taking into consideration utilizing AOP on your services layer to immediately incorporate the ACL info with your solutions layer procedures.
- The code piece is fairly self-explanatory, except the insertAce method.
- In the instance over, we're fetching the ACL related to the "Foo" domain object with identifier number 44.
- We're after that adding an ACE to make sure that a principal named "Samantha" can "administer" the object.
When 2 people enter into a quarrel, it can be hard to know what you ought to do. There are several steps you can require to soothe the aggression, but it is necessary to maintain your own safety initially. Before you get included, have a clear concept what you need to do, to ensure that you can select the most effective option. Temperature level testing is necessary in maintaining your tenants, employees, and also customers risk-free; as well as an important device that is essential the resuming efforts of the USA.
This choice benefits those that have comprehensive experience however wish to plainly highlight certain abilities or qualifications that establish them apart. If you do not see any clues about company society noted in the work summary, look into Undoubtedly Company Pages or review the employer's site for additional information. Did you ever obtain recognition for fulfilling a specific goal or excelling in a specific area? If so, your skills likely aided you in reaching this success.

A bodyguard ought to constantly be alert and taking notice of his or her environments. You must not need to be worried concerning your bodyguard giving right into disturbances or losing emphasis. Staying constantly careful is a core attribute of the optimal security specialist. A quick evaluation would truly make our day (it'll only take 15 secs) if you have time.
What is your career objective example?
If you see a security guard or police officer, tell them. They will break up the fight as they are trained.
Objectsecurity. The Security Policy Automation Company.
Our code nerds as well as Human Resources professionals are happy to present our new Free Resume Builder software application to aid you land extra meetings in today's competitive task market. We give HR-approved return to design templates, integrated task description bullet point phrases to choose from, as well as very easy export to MS Word and PDF. Last but not least, don't forget to highlight the reality that you have a security guard permit, particularly if it's an armed security personnel certificate. Licensing demands differ from one state to another, however the even more verifiable evidence there is that shows you have legit training, the far better. Army service is a HUGE marketing factor, so you'll want to make sure to highlight the moment you spent and the training you received in your military-to-civilian return to.
While the appropriate gatekeeper ought to have the ability to connect and also work in a team, she or he ought to likewise have the ability to function well alone. Your bodyguard ought to have the ability to perform his or her tasks without a supervisor.
wikiHow is a "wiki," comparable to Wikipedia, which means that most of our short articles are co-written by multiple writers. To create this article, 19 people, some anonymous, worked to modify as well as improve it over time. If they are intoxicated, armed, or plainly a greater than qualified competitor, it may not be a good situation to get associated with. Recognize individuals intensifying the altercation, prior to you make a decision to conflict.
What skills should I list on my resume?
1. Reverse chronological resume format. This is the bread and butter choice for most job seekers. It's also the most simple resume format and the one recruiters see the most, which can make a reverse chronological resume seem 'ordinary'.
As a bodyguard, she or he should be effective without instructions or oversight. You ought to try to find a person who has customer care training and also experience. This is due to the fact that your bodyguard will certainly be dealing with those around you at all times, consisting of customers, visitors, or clients.
What is Things Guard?
What is Things Guard?
The meaning of "guard" is an uncertain one. It can be a job title or it can be a term made use of to define a group of individuals operating in conjunction with the police. What is very important is that guard tasks are conducted based on the nationwide safety and security regulation.
Security personnel tasks are executed on an individual basis as well as consist of a variety of jobs which remain in accordance with the safety laws of the country in which the guard is utilized. There are different types of security personnel work that are available, such as the ones that handle the protection of structures and also individuals inside them.
There are guard activities that are done in order to safeguard the premises of a structure from burglars. The security personnel are required to literally stop a burglar from entering the building or to stop him from getting in the building when the security guard is not present. The guards are also expected to arrest anybody who is attempting to enter the building. They are additionally expected to physically limit any individual that tries to go into the building illegally.
There are security guard tasks that are done in order to secure individuals in the structure from the aspects, for instance, if the structure is subjected to the risk of fire or a fire. For instance, the guard will certainly be expected to be present at a fire exit or a smoke alarm in order to alert the police and also the fire department in situation there is a fire. Other security personnel activities include the protection of individuals that work in the building. If the guard notices a person who is under threat, then she or he should be notified instantly.
There are guard duties that are done in order to protect individuals that are inside the structure from theft. For instance, the guards are anticipated to literally protect against an intruder from entering the building if she or he is detected lugging a tool. If the trespasser tries to get in the structure, then he or she will certainly be shot or eliminated, unless the tool is contained inside a building security tool.
An additional guard task is that of shielding the security guards from the bad guys inside the structure that are not expected to be there. These consist of the guards from being robbed, or the guards from being injured by the offenders that exist. The guards are additionally supposed to shield the police officers inside the structure from the criminals if they are inside the structure.
There are additionally guard veel oplossingen op de markt that are executed in order to protect the residential or commercial property of the person or the business being secured. The guards are anticipated to protect the building of the business from burglary, damages or devastation, or loss, and also sometimes, they are also anticipated to secure the structure from vandalism. The guards are likewise expected to be in a setting to avoid an individual from going into or coming inside the structure if he or she is a possible lawbreaker.
The security guard tasks that deal with the residential or commercial property of the business are extremely essential due to the fact that the firm might be sued for problems if the firm was the one that was the target of the criminal activity or if the criminal offense occurred on the firm's building. The company might have to make restitution to somebody who was hurt or killed on the property. The company might likewise be demanded clinical or funeral costs if the business was a victim of criminal offense. The company might be held liable for lost wages if a consumer or worker is hurt because of the business's residential or commercial property.

Patents Assigned To Object Security Llc
5 Qualities Of A Great Security Officer
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Examining your skills as well as establishing locations of toughness as well as weak points to improve upon is the primary step to touchdown your suitable profession. By practicing and also applying crucial thinking, professionalism and trust, teamwork and also job principles, written as well as dental interaction, and also leadership abilities, you will certainly end up being more desirable to several employers. In many careers, written communication skills are just as important as oral interaction abilities. You can begin to boost your written communication abilities by organizing your ideas.
How many types of security guards are there?
As touching someone without lawful reason can be considered assault same with boucers they can only physically touch you should you need to be removed from the premises, restrain you from causing harm to yourself or others or are in need of aid also if you are being threatening towards a security guard or a boucer the
Private security employees in Johannesburg throughout the 2010 Globe Cup. The type An and Type B security solution are progressively integrated with residential property monitoring solution, though the limit between these two industries is uncertain. Type D allow owner was permitted to develop, set up, and repair work security devices. Have passed a required 16-hour training program and have been approved a certificate of the training course.
Professional Driving Ability
Every one of these internet sites and apps can only be developed by people with the required mobile and also web development skills. As werkzaamheden beveiliger as well as internet technology has progressed, increasingly more companies have looked to shadow computer as a convenient data storage space and monitoring service. This implies that people that have the abilities to handle and build cloud networks are in high demand. This is both a benefit and a curse for all types of designers.

Whizrt: Substitute Intelligent Cybersecurity Red Group
If you have never ever felt threatened at work, ask if you should discuss a danger run into in your exclusive life. Ideally, these dangers should have originated from other people, due to the fact that your response is meant to indicate how you will certainly respond to risks in your job as a guard.
Add Your Contact Info The Right Way
The capability to assess data and afterwards use that information for the benefit of your company is exceptionally helpful. Soft skills on the other hand, are not only beneficial throughout multiple sectors, but are a terrific device for sticking out from various other candidates that all have the very same hard abilities.
While it suggests your skills are a lot more popular, it additionally implies there are a variety of brand-new devices you may require to learn in order to build an effective occupation. The capacity to convince consumers to purchase a company's solutions or products will constantly be indispensable to prospective employers. After all, success in advertising straight correlates to a boost in income. While they might not be hard abilities themselves, licenses as well as qualifications are excellent for verifying to potential employers that you possess certain sought after capacities. Data evaluation abilities are extremely valued throughout a wide array of markets-- not just in financing.
- A few other program or service is using your data or folder simultaneously, avoiding you from modifying its authorization setups.
- Give opportunities on the cube's measurements and the analytic office.
- A basic reactivate must be more than sufficient to fix the problem if this is the case.
- To attempt taking possession of the object, that includes consent to see its residential properties, click Modification above.
If you have actually never ever really felt endangered by another human being, ask if a few other kind of risk (a quake, for instance) may be thought about appropriate. Talk regarding just how you used team-based problem-solvingin some various other kind of setting if you do not have previous experience in security. For these scenarios, you can highlight your capabilities by showing how you utilized them to achieve essential objectives for your company. This is done by inhabiting your expert experience area with your achievements. Numerous brand-new internet sites are produced every 2nd, and also on mobile, over 6,000 applications were released each day in the initial quarter of 2018 on Android alone.
Although essential assuming abilities are what employers need and also find most important, the typical company thinks current grads are just "rather competent" in vital believing skills. This means that, while companies believe vital assuming skills are 99.2% necessary, just 55.8% of grads excel. The ultimate objective of going to university is not just to get the level, however to land a profession also. Obviously, employers wish to make sure you are gotten the task by having the proper degree, yet they additionally need to recognize if you have the ability also.
When you are composing, proofread your work to see if it sounds cluttered, like your rambling or like the ideas do not stream. If this is the case, try creating a synopsis for your work initially, to make sure your ideas remain in a natural order, and afterwards begin composing. Another basic concern may simply be your own uncertainty in your writing.
The Types Of Security Guards
Throughout your day-to-day classes, tasks and work routine, you have opportunities to continue creating your professional abilities. These skills can be created through straightforward jobs such as being punctual as well as having an expert mindset. They likewise might be developed through even more lengthy tasks. Although crucial reasoning can be shown in the class, it requires to be used throughout research studies and also real-world experiences so you can make a routine of using critical reasoning in your every day life. According to the National Association of Colleges and Employers, critical assuming abilities are the top concern for a company to employ a person.
What are your top 3 skills?
The security guard may arrest a person when that person has committed a felony, but only if a felony has actually been committed. If the offense is not a felony it must be committed or at least attempted in the presence of the security guard before a citizen's arrest can be made.
The visibility of a burglar or of an object that individuals are, for reasons of security, not allowed to bring onto the facilities or location or any other facilities or location. They even had the option to pick exactly how often they would be triggered to give a security code as their 2nd element.
What is security guard in basic?
As an SHE Advisor, you will be responsible for managing all the Health, Safety and Environmental issues relating to the site.
Security Vs. Visibility
Supplying Maryland, Washington DC & Virginia with Security Solutions integrated with the current Innovation as well as Experienced Worker for a complete service to all of your safety needs. Remote video clip monitoring agents are trained to observe in extraordinary detail. Their job is to understand the website format as well as authorized workers. They keep an eye on security electronic camera video footage to report and also recognize anything outside of the norm. High danger degrees, such as scenarios involving violence or prized possessions, commonly need armed guards.
What are good skills for a security job?
A security officer generally has no arrest authority on public roads. The only thing an officer can do is keep you in sight, call police and and report the reason for the guard's report and observation. Not on a public road , but if you were on private property you could be asked why your there or just drive away.
How to Learn Object Security Personnel
Exactly How to Find Out Things Security Guard
There are various sorts of things security, but one of the most usual is called "dome guarding," or simply "domeing." It is a technique used by security personnel to shield home from being broken into or stolen.
Dome securing is a method that is made use of by guard to make a border around any location that is utilized for service. In order to do this, security personnel would certainly walk around the location and area a number of dummies around the building. Periodically, the guard would have a possibility to walk around the boundary of the residential property and also "dome" the dummy sets. If the security personnel did not successfully dome the dummy, they would certainly go back to where they were initially positioned.
Domeing is among https://www.dutchcrowdsecurity.nl/objectbeveiliging/ of guard activities, since it is a relatively easy task. It does not need a lot of devices or even a lot of technique. Consequently, this is among the easiest kinds of security personnel task to learn.
Although domeing is a rather simple sort of guard tasks, some individuals may have troubles with it due to its simplicity. A guard might not recognize the very best method to position a dummy around their residential property. This may additionally cause the guard not succeeding in their domeing tasks.
In order to succeed in what is referred to as domeing, a security personnel must understand the concepts of just how the process works. If they do not understand the process, they will not succeed. Below are a few ideas to help security guards find out the process of doing.
The initial thing that a security guard should do when they are carrying out object security personnel tasks is to attempt to comprehend what is going on around them. When they recognize what is going on, it will certainly be easier for them to correctly position themselves to make a successful dome. This will make their work much easier.
The second thing that a guard must do when they are in doing tasks is to have a good understanding of what their surroundings are. By recognizing what is around them, the security guard will recognize what kind of things they are most likely to encounter during their job day. This will certainly make it simpler for them to position the dummy in the most effective way.
The last point that a security personnel should do when they are in doing is to ensure that they look out to any potential burglars. If a guard looks out to any possible trespassers, they will certainly be able to discover any kind of motion when they are around the residential property.
By looking out to any kind of possible burglars, the security guard will be able to easily determine any type of movement when they are around the home. This will assist them to shield the property while they are performing their jobs.
If a guard has an understanding of what they are going to be carrying out in a particular environment, they will have the ability to make an accurate evaluation of the scenario when they are working. This will certainly allow them to secure the residential or commercial property in the best means feasible. It will certainly also help them to make their job a lot easier.
If a security personnel is uncertain of what to anticipate, they can most likely to an expert because field. As an example, a security guard can speak to a professional in the armed forces or a police officer. These professionals will certainly be able to help them understand what to anticipate throughout a specific circumstance. This will aid them to be as efficient as feasible when they are working.
Learning the strategies of item security guard is really essential for security personnel. It is necessary that a security personnel understands exactly how to appropriately safeguard home. This is one of one of the most vital kinds of security guard task that they can find out.

3 Kinds Of Security Guards And Also What They Do
Security Personnel Resume Sample & Creating Tips
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
A customer care division has an objective to gauge client fulfillment as well as benefit agents that are exciting clients. A sales team establishes the purpose to automate lead certification with the goal of boosting sales conversion rate and also lead worth.
As an example, "65% of the citizens of Malott Region do rule out teen pregnancy to be an important trouble for the neighborhood." Your organization has established (or spruced up) its vision and objective statements, and also is ready to take the following action in the planning procedure. Keeping participants of the organization working toward the exact same long-term goals. Info worrying the objective can be accumulated, discovered, or acquired.
What is security guard in basic?
One of the main functions a security guard has is to protect people and maintain safety. Often times, the watchful presence of a security guard is enough to deter criminals and prevent incidents. People are often grateful for the presence of a security guard, and helping them feel comfortable and safe can be rewarding.
If you submit a neat, appropriately arranged file, you'll encourage the recruiters to invest even more time on your CV. Envision you are the employer as well as you have to evaluate 250 job applications. In the hiring market, nowadays there's nearly no official difference in between a Curriculum Vitae as well as a resume. It's the same point that Brits call a CV and Americans-- a return to. Exactly how to compose a curriculum vitae even if you have no experience.

Specialist Driving Ability
What are good skills for a security job?
A security officer generally has no arrest authority on public roads. The only thing an officer can do is keep you in sight, call police and and report the reason for the guard's report and observation. Not on a public road , but if you were on private property you could be asked why your there or just drive away.
Opening up a second place is a goal in a restaurant's plan to scale its service. Passing lees meer over beveiligingsbedrijf is a goal that is essential to accomplish the objective of finishing from a college with a level. Goals are recognizable as well as meaningful steps on the path to an objective. The initial one comes from a client service rep desiring to begin a new profession as a shipment driver.
Whizrt: Substitute Smart Cybersecurity Red Team
Don't be just one of those candidates stuck in the nineties that assume they have to include every single information about their lives on their CVs. Yet not as tight as an ID picture if so-- make certain to make use of an expert looking picture. And also, most of the time, after you send your CV, it's going to be published in black ink on white paper. An improperly formatted CV, on the various other hand, will obtain you thrown out in the first-round testimonial.
What is security guard in basic?
As an SHE Advisor, you will be responsible for managing all the Health, Safety and Environmental issues relating to the site.
Include Your Get In Touch With Info Properly
- We have a single row for every single domain object circumstances we're keeping ACL approvals for.
- ACL_OBJECT_IDENTITY stores info for each one-of-a-kind domain object circumstances in the system.
- Nonetheless, the very first pairs your consent examining to your company code.
- The main problems with this consist of the enhanced difficulty of system testing as well as the reality it would be harder to reuse theCustomer permission reasoning elsewhere.
Fitness as well as StrengthSecurity guards must be planned for the opportunity of physical fight. Whether this takes the kind of chasing after a thief or breaking up a fight, guards need to preserve affordable health and fitness and also strength to stay on par with potential transgressors. They have a tendency to be reasonable people, which indicates they're independent, steady, relentless, real, practical, and thrifty. They such as jobs that are responsive, physical, sports, or mechanical. Some of them are also conventional, indicating they're conscientious and also conservative.
You send your CV as well as you breathlessly wait on the call-back. Because you intend to offer plenty of attention to both, you may not have much room left for other sections, such as a resume recap, volunteer job, passions, and so on . And your personal story better impress recruiters, or else, no job for you. In a nutshell, the function of your resume is to inform a (short) tale about that you are, what you have actually done and what you can do.
Objectsecurity. https://www.blackplanet.com/pailchalk7/message/21624046 .
Regardless of having no experience, the candidate makes a clear deal. She held a couple of part-time personal assistant jobs where her duties resembled those noted in the job advertisement. And also, she completed a legal assistant course and also obtained a qualification. When you're done, Zety's resume contractor will certainly score your return to as well as inform you precisely how to make it better.
The Kind Of Security Guards
In the incorrect example, she just stated what she desired out of the work. All other candidates are searching for an admin assistant duty. In the best instance, she refers to skills she learned with teaching fellowships, volunteering, as well as in university. As well as she clearly shows how her credentials will benefit the employer.
Profession Recommendations Boost your job with professional tips and methods. Find out just how you can obtain a new work or improve the one you have.
Highly-engaged sales rep with a BS in Biology, seeking to enhance sales numbers for Azult Medical. Test return to made with our builder-- See even more layouts and also produce your return to here. Press Web page Read initial information insights to boost your reporting.
Security Vs. Presence
At colleges, in parks, and also at sports arenas, guards do group control, oversee auto parking and seating, and direct website traffic. Your company will require to take a great consider its sources, in addition to speak with specialists that have a sense of what is not just possible, however likely. As an example, you might ask participants of organizations who have actually done comparable things, or scientists in your subject area what they believe makes sense. Baseline information may also measure community attitudes in the direction of a trouble.
What are your top 3 skills?
The security guard may arrest a person when that person has committed a felony, but only if a felony has actually been committed. If the offense is not a felony it must be committed or at least attempted in the presence of the security guard before a citizen's arrest can be made.
Leading 10 Difficult Skills Employers Love
Security Police Officer Return To 3, Instance, Crash Avoidance, Event Examination, Work Duties, Jobs
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
This extends to both Appian Designer and also Tempo or websites, where it applies. Once, a group or individual should only be detailed in the function map. All objects To stay clear of confusion as well as make certain that Appian gives a team or customer the appropriate authorization degree, you ought to just detail a group or customer in the role map once. It will constantly appoint that team or user their greatest approval degree if Appian finds the very same team or customer in the role map even more than as soon as.
Appian advises attending to the specific cautions on the suitable parent so that all other objects embedded below that moms and dad will certainly likewise obtain the very same upgrade. You may have to trace via a number of layers of inherited security to find the root moms and dad on which the certain warnings first show up. You currently do not have administrator approvals for this object. Make sure to include on your own to a manager group in this role map before continuing.
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
Expert Driving Ability
No basic customers will certainly be able to provide this object, which includes editing and enhancing its security or deleting it. All items It is a finest technique to designate at the very least one Manager team to each challenge make certain that developers aside from the object's developer will certainly be able to carry out the object. No basic individuals will certainly be able to see or make adjustments to these things.

Whizrt: Simulated Smart Cybersecurity Red Team
How do I write a resume for a security guard?
security. Security means safety, as well as the measures taken to be safe or protected. Often this word is used in compounds such as a security measure, security check or security guard. The security department in a business is sometimes just called security.
Appian recommends that you do not give 'Default (All Various Other Individuals)' Manager approvals, and instead grant certain groups administrator rights. View and upgrade the parent's security to fix inherited cautions. All items that can inherit security This caution indicates that of the object's parent things has certain cautions that need to be dealt with.
Choosing administrator as the default enables all individuals to administer this object, consisting of anyone listed in the duty map with a permission level besides Reject. Appian suggests providing manager accessibility to specific teams instead. This is due to the fact that the 'Default (All Various Other Individuals)' Administrator consent will be granted to all groups and also customers in the function map besides those with explicit Deny consents.
Include Your Call Info Properly
Permissions The ACL reveals which groups as well as customers are given accessibility to the chosen object, and also their corresponding authorizations. You must establish object security prior to other users can access them. When an object owner shares gain access to with them, customers acquire accessibility to items. Owners can show to specific users or with whole groups, admitting to everyone within that group. A user can automatically share objects with anybody else in the groups to which they belong.
- Examining that security has been configured for all objects packaged for implementation.
- For example, a group's legal rights to a private area are determined by its area rights across the work area.
- Altering security approvals from overwrite acquired security to acquire security and the other way around may involve a wait time for 50,000 documents or even more.
- Providing designers with a Security Summary view of each application.
- If https://www.openlearning.com/u/callperiod30/blog/WhatIsItemProtectionWhatDoesASecurityPersonnelDo/ happens, a notice appears to inform you of the effect of the adjustment.
- As an example, a site could have 3 Customer groups in its security duty map.
Appian advises providing customer accessibility to particular teams rather. https://ourdoings.com/mathorsure37/ is an ideal method to approve specific teams Audience legal rights to understanding centers as opposed to establishing 'Default (All Various Other Customers)' to audiences. Doing so guarantees that document folders and records nested within knowledge facilities have actually explicit viewers set. objectbeveiliging will certainly be able to begin this procedure version as an action or relevant activity. This shows that no basic user will certainly have the ability to begin this procedure model.
Appian has found that this process model might be made use of as an action or associated activity. No standard users will certainly be able to start this process model without having at the very least initiator permissions if that is the situation. If it discovers that the process design is referenced by a constant or choice, refine models Appian will present this caution on a process design. In this situation Appian can not assure that an Initiator, Customer, Editor, or Manager team is called for due to the fact that it does not understand how you mean to utilize the procedure design.
Warning Suitable Object Types Additional Details Individual customer identified. All things Only using teams makes it easier to manage security since you can quickly add or eliminate a customer to a team, which automatically updates every one of the function maps that referral that team. Using groups guarantees that customers have the appropriate authorizations to objects as objects are pushed to higher environments.
All objects that do not acquire security This caution is just displayed when you are logged in as a basic customer and are creating an object that does not acquire security from a parent. This caution indicates that you have actually removed on your own as a Manager of the object and will not be able to erase the object or update its security after creation. Picking visitor as the default permits all users to view this expertise facility, leaving out any person noted in the function map with a various permission degree. This likewise applies to the papers as well as folders that acquire from it.
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
The Kind Of Security Guards
The authorizations list on the Reliable Accessibility tab is empty by default. Add as well as remove participants to the listing to see the kind of accessibility they need to the object under the picked security kind. Adjustment the security type to see how permissions are influenced.
What you mean by security?
Good security protects the people, reputation and profitability of your organisation. This guide contains best practice to help you create an effective risk management strategy; one that covers the identification, assessment and mitigation of the threats your organisation might face.
Add teams with one of the previously defined approval degrees if you are intending to allow individuals to start this procedure model. The opportunities are layered so that, as an example, a user with SELECT data security on Software must additionally have SELECT object security on the PRODUCT measurement as well as the Worldwide analytic work area. Users likewise need CHOOSE opportunities on the views of the dimensional objects. The advantage of applying split object security is that it is feasible to implement stringent security designs, and control security to items and also functions at a granular degree. Appian suggests frequently checking your applications, as well as assessing their Security Recap to guarantee that the appropriate customers have the appropriate authorizations to all of your applications and also their attributes.
Security Guard Resume Example & Composing Tips
5 Elements Of An Efficient Safety And Security Society
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Job-specific skills can be contrasted withtransferable skillslike interaction, organization, discussion, planning, team effort, and also time administration, which are required in a wide array of work. For instance, if you are requesting a task in education and learning, you could include a "Computer system Skills" listing and a "Language Abilities" checklist. When you are offering information of the skills you created in a teaching fellowship, work or work experience positioning, mirror the expertises provided in the task description as well as provide instances of the most relevant skills first. This is about knowing how a business or industry jobs and also what makes a company tick. Revealing that you have an understanding of what the organisation wishes to attain via its solutions and items, and also how it contends in its industry.
Specialist Driving Capacity
Grad companies put a lot of focus on discovering prospects with the right skills as well as competencies for their organisations. Depending on the career sector and also profession you pick to work in, there might be really certain abilities, abilities and also understanding needed to do the work. You'll need to provide instances of these important expertises in your task applications and also meetings to thrill employers and also obtain worked with. Additionally prepare to address tough questions concerning your condition at your previous or current setting, however take care right here. " Stand up to need to air all your filthy washing and attempt to keep points neutral. Maintaining it stylish when speaking about your last job shows you want to do the very same thing in your brand-new work also," he recommends.
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
Whizrt: Simulated Smart Cybersecurity Red Group
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
In 2015, the unemployment rate for details security supervisors averaged.9%, as we reported in High CISO work prices implies lack for security sector. L1S attributes give the advantage of simple as well as fast general visual verification of identification details without the use of specific or specialized tools. Nonetheless, a specialist with particular devices will certainly be required to determine imitations or tampering.
" My very own image is far from suit-and-tie. Yet even if you're a kilt-and-Vibram type of person, be aware that a job interview is still a semi-formal occasion," states Adams. " I've had prospects do Skype interviews being in hotel restrooms, roll right into on-site meetings putting on jean shorts and t-shirts, as well as make use of language I won't repeat during technological testings," she states. Understanding something concerning the company also needs to consist of understanding something, whenever possible, regarding the person carrying out the interview. " This includes their job history, technical background, as well as any type of published research," says Amit. C. Yerrid, elderly security consultant at FishNet Security, pertaining to beginning settings.
What is security guard full form?
As meld u aan bij uw beveiligingsbedrijf plus ... , you must appoint a 'competent person' to help you meet your health and safety duties. In general terms, the definition of a competent person is someone who has the necessary skills, experience and knowledge to manage health and safety.
Just how to list difficult skills to make up for what you do not have in experience. ( As well as learn just how to utilize them on a resume to rack up interviews.) Good information? And also, there is no demand to consist of skills that do not relate to the work available. Unless you're applying to delight at youngsters's events, your capacity to make balloon animals should not be consisted of.
He says most would certainly be surprised at exactly how valuable sharing such information can be to the recruiter. " I constantly locate something security-relevant that can be achieved with those skills," Amit states. And also he includes that it assists to assure the interviewer that the candidate isn't a one-trick-pony that is entrenched with Nessus or Metasploit as well as can't be really utilized in a real-life pentest," he claims. Not unsurprisingly, with the huge distinction in organisation culture today, picking the proper outfit for a meeting isn't as simple as it once was. " I like the society of info security, in which your CISO may well have a Mohawk," claims Adams.

- To read more regarding object-specific security settings as well as authorization degrees, see the security section in each layout object's page.
- This first image reveals the security duty map for ABC Rule Folder.
- Teams, duty maps, security inheritance, layered security, as well as object presence are essential principles to find out in order to completely recognize object security.
- Notification that ABC All Admins have Administrator approvals to this process design while ABC All Customers just have Viewer legal rights.
- Note that ABC Policy Folder is a top-level object since it does not have a moms and dad object.
Add Your Call Details Properly
What you mean by security?
Good security protects the people, reputation and profitability of your organisation. This guide contains best practice to help you create an effective risk management strategy; one that covers the identification, assessment and mitigation of the threats your organisation might face.
" are very vital concerns to hiring supervisors for a number of factors. Police officers also require to preserve precise logs for their companies and assemble everyday records to hand over to the inbound change. A gatekeeper preserves consistent vigilance at his workplace observing and reporting on any type of abnormalities or dubious activities and also stepping in or calling for aid if there is illegal activity. The policeman has to look out no matter the hr, which is frequently hard particularly at night in cool as well as dark conditions functioning alone.
I typically compare work interviewing to dating (with any luck, dating goes to the very least a little bit a lot more fun for you). No day wishes to listen to," You were the just one who would go out with me." It coincides with task interviews. You need to charm the company and talk about why the position was created you. In this situation, the prospect is talking to for a really popular company.
This prevents laid-back trespassers from accessing to, as an example, inscribed confidential information inside an embedded chip or various other means of inscribing. Technologies at this level consist of wise chips, magnetic strips, Radio Frequency Identification (RFID), contactless chips or clever chips with ingrained identification and also biometric information. With the right tools, L2S plans permits the capability to record, sign up and also validate document holders' identification details and also, of late, biometric identity info.
The encoded data is limited by the chip memory size and capability. A customized gain access to mechanism (i.e. the reader as well as encoder gadget) is called for to acquire accessibility to the pertinent information resource and also create data onto the embedded medium. Level 1 Security (L1S) SURFACE AREA Data-- Level 1 Security provides the most affordable degree of security. This basic security requirement is described as obvious security printing methods (or methods requiring unique optical devices). These are complemented by used security features, such as OVD's or iridescent stripes, warmth delicate ink, optical variable ink and various luxury printing approaches or innovations.
In a situation similar to this, the tendency for numerous prospects is to essentially respond to," Well, it's JP Morgan. Duh." In today's task market, that's not going to suffice to establish you aside from other prospects, even if your resume is excellent. " as well as it's sister inquiries like "Why do you intend to work for us?
How do I write a resume for a security guard?
security. Security means safety, as well as the measures taken to be safe or protected. Often this word is used in compounds such as a security measure, security check or security guard. The security department in a business is sometimes just called security.
You remain in the middle of a career change or have voids in your employment. Show managers and also organizers exactly how beneficial your skills are with a terrific practical resume. Listing them in a different resume area if you have certifications that back up your skills. Consist of the name of the certification and the year you obtained it. In contrast, soft skills are your abilities and traits not one-of-a-kind to any type of task-- assume collaboration, time administration, leadership, or empathy.
Guard Meeting Questions As Well As Responses
Top 5 Skills Companies Look For
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
It has the security advantages of Oracle Data source, which leads the market in security. You do not require to expose the information by transferring it to a stand-alone database. You do not need to carry out security on a different system. And also you do not need to jeopardize your information by saving it in a much less safe and secure setting than Oracle Database. Oracle OLAP safeguards your data utilizing the common security mechanisms of Oracle Data source.
AD Teams can be included in the Tableau Server, and after that set to sync on a timetable. Every person that can see material on the Tableau Server requires to be an individual on at least one Website in the Tableau Web server (this consists of the default Site). Enter the adhering to commands in the window and also see to it you press Go into after inputting every one. Wait on the "Operation completed effectively" message or something similar to know that the method worked.
Since someone can share with any individual in the very same team, they can potentially share restricted columns. That 'outdoors' person now has accessibility to the income info.
If object beveiliger place everyone in your company right into the same group for RLS, they can show anyone in the company. If they are not designated to a team that has gain access to, they do not see any kind of information. IBM will certainly offer your email, first name as well as last name to DISQUS when you sign in to comment. That details, together with your comments, will certainly be governed byDISQUS' privacy policy.
Making it easy for programmers to edit an existing object's security any time. Similarly, a record type might have several Customer groups, but a programmer could specify that only one team is permitted to utilize the record related action by providing a visibility expression.
What you mean by security?
Good security protects the people, reputation and profitability of your organisation. This guide contains best practice to help you create an effective risk management strategy; one that covers the identification, assessment and mitigation of the threats your organisation might face.
Expert Driving Capacity
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
Hence, there is a solitary row for each unique principal or GrantedAuthority. When utilized in the context of getting an approval, a SID is normally called a "recipient".
Whizrt: Substitute Smart Cybersecurity Red Team
By commenting, you are approving theDISQUS regards to solution. If a customer drags a folder with item-level security into another folder, the brand-new kid folder inherits the parent folder's security. By default, collections are arranged in coming down order, from collections with one of the most objects to groupings with the least. You can reverse this type order any time by clicking Switch Sort Order in the leading right-hand edge of the dialog (F).
- The cornerstone of information security is the management of customer accounts and roles.
- ThoughtSpot's Advanced Security mode is contrary of the default liberal mode.
- Similarly, you can only see the data in a worksheet to which you have access if you have explicit approvals to its parent table object.
- Individuals open a link with Oracle Database with a customer name as well as password, as well as they have accessibility to both relational as well as dimensional things in the exact same session.
Include Your Call Details The Right Way
In such situations, we suggest that you deal with your ThoughtSpot support group to enable the Advanced Security Setting on the pertinent clusters. Bear in mind that individuals within a team can share with each other.
What is security guard full form?
As an employer, you must appoint a 'competent person' to help you meet your health and safety duties. In general terms, the definition of a competent person is someone who has the necessary skills, experience and knowledge to manage health and safety.

In 2019, ObjectSecurity released an alpha variation of an U.S. United States Navy SBIR moneyed VAPT automation tools, which automatically assess both IP systems/networks and also ingrained devices (via non-IP ports) for software program susceptabilities. Intrigued in learning about the benefits of Security Plan Automation? ObjectSecurity's mission is to streamline, enhance and also automate security for the complex, interconnected IT landscapes most organizations have to manage today. Our core product is OpenPMF, the internationally leading as well as awarded security plan automation solution.
How do I write a resume for a security guard?
security. Security means safety, as well as the measures taken to be safe or protected. Often this word is used in compounds such as a security measure, security check or security guard. The security department in a business is sometimes just called security.
Please note that our out-of-the-box AclService and relevant data source courses all utilize ANSI SQL. This ought to as a result work with all significant data sources. At the time of composing, the system had been efficiently examined using Hypersonic SQL, PostgreSQL, Microsoft SQL Web Server and also Oracle. ACL_SID permits us to uniquely identify any major or authority in the system (" SID" stands for "security identification"). The only columns are the ID, a textual representation of the SID, as well as a flag to show whether the textual representation refers to a primary name or aGrantedAuthority.
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
Furthermore, you can likewise make use of the Windows Logo Key + R key combination in order to bring up the Run dialog box. Type in "cmd" in the dialog box which appears and make use of the Ctrl + Change + Go into key mix for admin Command Trigger. Click heaven Select a major button from the top of the web page and click Advanced from the brand-new Select User or Team home window. Browse to the folder or documents that you which to change the consent settings for. Browse to the Security tab as well as click the Advanced switch at the bottom.
Security Vs. Exposure
Click the Include switch in the new window which stands out up as well as click the Select a principal switch at the top. This approach works for a variation of Windows older than Windows 10. Use the Windows + R key combination on your keyboard in order to start the Run dialog box and also type in "msconfig" before clicking OK. Grant advantages on one or more dices and also their dimensions. Your data is kept in the data source when you use Oracle OLAP.
16 Domain Name Object Security
Top 5 Skills Companies Look For
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
It has the security advantages of Oracle Data source, which leads the market in security. You do not require to expose the information by transferring it to a stand-alone database. You do not need to carry out security on a different system. And also you do not need to jeopardize your information by saving it in a much less safe and secure setting than Oracle Database. Oracle OLAP safeguards your data utilizing the common security mechanisms of Oracle Data source.
AD Teams can be included in the Tableau Server, and after that set to sync on a timetable. Every person that can see material on the Tableau Server requires to be an individual on at least one Website in the Tableau Web server (this consists of the default Site). Enter the adhering to commands in the window and also see to it you press Go into after inputting every one. Wait on the "Operation completed effectively" message or something similar to know that the method worked.
Since someone can share with any individual in the very same team, they can potentially share restricted columns. That 'outdoors' person now has accessibility to the income info.
If object beveiliger place everyone in your company right into the same group for RLS, they can show anyone in the company. If they are not designated to a team that has gain access to, they do not see any kind of information. IBM will certainly offer your email, first name as well as last name to DISQUS when you sign in to comment. That details, together with your comments, will certainly be governed byDISQUS' privacy policy.
Making it easy for programmers to edit an existing object's security any time. Similarly, a record type might have several Customer groups, but a programmer could specify that only one team is permitted to utilize the record related action by providing a visibility expression.
What you mean by security?
Good security protects the people, reputation and profitability of your organisation. This guide contains best practice to help you create an effective risk management strategy; one that covers the identification, assessment and mitigation of the threats your organisation might face.
Expert Driving Capacity
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
Hence, there is a solitary row for each unique principal or GrantedAuthority. When utilized in the context of getting an approval, a SID is normally called a "recipient".
Whizrt: Substitute Smart Cybersecurity Red Team
By commenting, you are approving theDISQUS regards to solution. If a customer drags a folder with item-level security into another folder, the brand-new kid folder inherits the parent folder's security. By default, collections are arranged in coming down order, from collections with one of the most objects to groupings with the least. You can reverse this type order any time by clicking Switch Sort Order in the leading right-hand edge of the dialog (F).
- The cornerstone of information security is the management of customer accounts and roles.
- ThoughtSpot's Advanced Security mode is contrary of the default liberal mode.
- Similarly, you can only see the data in a worksheet to which you have access if you have explicit approvals to its parent table object.
- Individuals open a link with Oracle Database with a customer name as well as password, as well as they have accessibility to both relational as well as dimensional things in the exact same session.
Include Your Call Details The Right Way
In such situations, we suggest that you deal with your ThoughtSpot support group to enable the Advanced Security Setting on the pertinent clusters. Bear in mind that individuals within a team can share with each other.
What is security guard full form?
As an employer, you must appoint a 'competent person' to help you meet your health and safety duties. In general terms, the definition of a competent person is someone who has the necessary skills, experience and knowledge to manage health and safety.

In 2019, ObjectSecurity released an alpha variation of an U.S. United States Navy SBIR moneyed VAPT automation tools, which automatically assess both IP systems/networks and also ingrained devices (via non-IP ports) for software program susceptabilities. Intrigued in learning about the benefits of Security Plan Automation? ObjectSecurity's mission is to streamline, enhance and also automate security for the complex, interconnected IT landscapes most organizations have to manage today. Our core product is OpenPMF, the internationally leading as well as awarded security plan automation solution.
How do I write a resume for a security guard?
security. Security means safety, as well as the measures taken to be safe or protected. Often this word is used in compounds such as a security measure, security check or security guard. The security department in a business is sometimes just called security.
Please note that our out-of-the-box AclService and relevant data source courses all utilize ANSI SQL. This ought to as a result work with all significant data sources. At the time of composing, the system had been efficiently examined using Hypersonic SQL, PostgreSQL, Microsoft SQL Web Server and also Oracle. ACL_SID permits us to uniquely identify any major or authority in the system (" SID" stands for "security identification"). The only columns are the ID, a textual representation of the SID, as well as a flag to show whether the textual representation refers to a primary name or aGrantedAuthority.
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
Furthermore, you can likewise make use of the Windows Logo Key + R key combination in order to bring up the Run dialog box. Type in "cmd" in the dialog box which appears and make use of the Ctrl + Change + Go into key mix for admin Command Trigger. Click heaven Select a major button from the top of the web page and click Advanced from the brand-new Select User or Team home window. Browse to the folder or documents that you which to change the consent settings for. Browse to the Security tab as well as click the Advanced switch at the bottom.
Security Vs. Exposure
Click the Include switch in the new window which stands out up as well as click the Select a principal switch at the top. This approach works for a variation of Windows older than Windows 10. Use the Windows + R key combination on your keyboard in order to start the Run dialog box and also type in "msconfig" before clicking OK. Grant advantages on one or more dices and also their dimensions. Your data is kept in the data source when you use Oracle OLAP.
What Is Object Security Personnel Activity?
What Is Object Security Guard Activity?
If you have actually been hired by a business or a specific to protect a person or something, then you might be required to carry out one or more specific security personnel activities. What are some of these security personnel activities that are necessary and also what is an example of what is essential?
Among the more usual security guard tasks is to make sure that a structure or area is risk-free, both for the person that is inside and the one that is protecting the structure. There are some things that you may need to do when you are shielding a location, for example you may need to see to it that there are no people inside the building or that a person who is trying to enter is not allowed to do so. This can be done by checking for possible access factors, which may be hidden or open.
When you are on guard responsibility, you might also have to deal with an item guard. These are generally really experienced individuals who can utilize a variety of various types of equipment to shield a things. These can include alarm systems, motion sensors, dynamites, and even a video camera to videotape the occasions of the area.
Among the other security guard activity that is typically done is that of maintaining a building or area secure from intrusion. There are various things that you can do in order to maintain an area risk-free and if you are in a position to do so you can be asked to make sure that a structure or area is risk-free and protected. It is feasible that you might be called for to perform a security check of a structure or area in order to make certain that there are no dangers, as an example you might need to look for feasible bombs.
One more security personnel activity that is required in numerous situations is to be able to protect people from injury. For instance, you may be needed to protect people who have been injured or that might remain in risk of falling into the water. This can be a vital and also frequently an essential job. If you are required to do this work, you will certainly more than likely be required to wear a diving mask, a life vest, as well as some kind of breathing apparatus, all of which are developed to stop people from drowning in case of an emergency situation.
Another essential security personnel task that is frequently needed is that of guaranteeing that a location is protected from criminal damage. This can consist of things like securing a structure from being burglarized. or triggering damages to residential property. http://www.beveiligingswereld.nl/ will need to ensure that a structure or location is safe and secure against criminal damage in order to stop any kind of damages or theft from taking place as well as to the property.
You will certainly probably additionally be required to keep track of any lorries that are being protected. This may be to make sure that you can make sure that the vehicles are in risk-free positions. You can likewise be asked to make certain that the cars are in proper functioning order as well as to avoid any damages from happening.
These are some of the guard activities that are most frequently required as well as it is easy to see why there are so many various kinds of guard responsibilities. It is also easy to see why you will require to be able to do these jobs. In order to be an effective security guard, you will certainly need to understand what the various duties are, and also to be able to do them correctly, you will require to have a particular quantity of skill, expertise, and also experience.

What Security Personnel Can As Well As Can't Do
Data And Object Security
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Each section has 2 components; on the left-hand side there is a function map (B), as well as on the right-hand side you will locate a list of every one of the items with that certain duty map (C). When creating new items that do not acquire security from a moms and dad by default, Appian will certainly advise you to establish object security.
What are your top 3 skills?
The security guard may arrest a person when that person has committed a felony, but only if a felony has actually been committed. If the offense is not a felony it must be committed or at least attempted in the presence of the security guard before a citizen's arrest can be made.
Professional Driving Capability
By utilizing theSecurityContextHolder.getContext(). getAuthentication(), you'll be able to access the Authenticationobject. ON - changes group gain access to and object security bypasses the office level security setups. Click Edit Permissions for a group to modify the group's object security rights. Click Add/Remove Groups to add or eliminate groups for which you desire to establish explicit object permissions if you set Overwrite Inherited Security to ON to change an object's security.
Whizrt: Substitute Intelligent Cybersecurity Red Group
What are good skills for a security job?
A security officer generally has no arrest authority on public roads. The only thing an officer can do is keep you in sight, call police and and report the reason for the guard's report and observation. Not on a public road , but if you were on private property you could be asked why your there or just drive away.
Throughout development, each procedure model will certainly call for that its own security be established. See the following area for a breakdown of which object kinds constantly, optionally, or never inherit security from moms and dad items. Audiences - Teams who can interact with a certain object as an end individual in Pace, sites, or ingrained. As an example, providing a team Audience civil liberties to a user interface gives them authorization to connect and also view with that said user interface from Tempo.

Add Your Call Info The Right Way
ON - modified team access and object security bypasses the office level security settings. The Security Summary shows a listing of object collections (A).
Objectsecurity. The Security Plan Automation Company.
We have a single row for every domain name object instance we're saving ACL consents for. Nevertheless, the initial couples your permission checking to your business code. The major issues with this include the improved difficulty of device screening and also the truth it would certainly be more difficult to recycle theCustomer consent reasoning elsewhere. Acquiring theGrantedAuthority [] s from the Authenticationobject is additionally great, however will not scale to lots ofCustomers.
- Customers likewise require SELECT privileges on the sights of the dimensional objects.
- Process models Appian will show this warning on a procedure version if it finds that the process model is referenced by a continuous or decision.
- If you are planning to allow users to start this procedure model, add groups with among the formerly explained permission degrees.
- In this case Appian can not assure that an Initiator, Audience, Editor, or Manager group is called for because it does not understand how you mean to use the process design.
- No basic customers will be able to begin this procedure model without having at the very least initiator approvals if that is the case.
What is security guard in basic?
As an SHE Advisor, you will be responsible for managing all the Health, Safety and Environmental issues relating to the site.
Create an AccessDecisionVoter to implement the security and open up the target Customer domain name object straight. This would imply your voter requires accessibility to a DAO that permits it to get theCustomer object. It would then access theCustomer object's collection of accepted users and make the ideal choice. You might seek advice from a collection within the Consumer domain name object instance to figure out which customers have access.
It is essential to understand that the variety of domain things in your system has definitely no bearing on the reality we have actually picked to use integer bit masking. Whilst you have 32 bits offered for authorizations, you could have billions of domain name object instances (which will suggest billions of rows in ACL_OBJECT_IDENTITY and also rather possibly ACL_ENTRY). We make this factor because we've located occasionally individuals incorrectly think they require a little bit for each potential domain name object, which is not the instance. ACL_OBJECT_IDENTITY beveiligingsbedrijf ideeën for each and every distinct domain object circumstances in the system.
At the time of the release of OpenPMF version 2, model-driven security was tied together with a model-driven development process for applications, especially for active service oriented architecture (SOA). Above rues says, user JARVIS can see Sheet kind object as well as object is Budget Analysis. Now, login with JARVIS, you will see Jarvis see "Budget Analysis" sheet only. COM things have actually lately been made use of by penetration testers, Red Teams, as well as malicious stars to execute side activity.
The Kind Of Security Guards
The code fragment is relatively self-explanatory, other than the insertAce method. The first debate to the insertAce approach is identifying at what position in the Acl the new entry will certainly be inserted. In the example over, we're simply putting the brand-new ACE at the end of the existing ACEs. The final debate is a boolean showing whether the ACE is denying or granting. Most of the moment it will be giving (true), however if it is denying (incorrect), the consents are effectively being blocked.
It is based upon an idea called model-driven security which permits the intuitive, business-centric spec of security requirements and the automated generation of enforceable safety and securities policies. http://peaknest2.over-blog.com/2020/07/what-is-object-security-personnel-activities-you-need-to-put-on.html was made to link the semantic space in between the policies that individuals take care of, and the plans that are technically executed.
The final method, opening up the Consumer directly from outside code, is possibly the very best of the 3. Furthermore, with every strategy detailed you'll require to write your very own access control listing (ACL) persistence and also business reasoning from scratch.
For example, after clicking the Develop switch for a brand-new procedure model, Appian will certainly ask you to assess and also set your process model's security. When developing brand-new objects that do not already inherit security from a moms and dad, advising designers to establish object security. Process model folders vary from understanding facilities, rule folders, and record folders because their security is never acquired by nested procedure version objects.
What a Guard Does and also How They Can Aid
What a Guard Does and Exactly How They Can Help
If you are associated with a specific industry in the protection industry or you are taking into consideration operating in the safety and security market, you need to recognize what is object protection and also what is safety and security. Right here are a couple of methods to find out about object protection and also safety.
Security guard activities and responsibilities are the important point you need to know. You will certainly locate that security personnel are the ones that are associated with safeguarding the residential property and also belongings of other individuals as well as residential or commercial property. They are in charge of checking, managing, reporting and also replying to criminal activities and also various other issues that might take place. These duties include expecting burglary, preventing invasions and also safeguarding the people that are in the residential property.
A lot of people are not knowledgeable about the obligations that a things security guard has. They are accountable for reporting any kind of type of building that might be affected by a crime or protection danger, especially if it is a delicate and also pricey building.
A guard will certainly need to take part in the process of looking for any type of questionable activity, specifically if there is a suspicious individual or suspicious product that may be found inside the building. This is necessary since if a criminal is going to try to creep right into the residential property, he or she will probably experience this procedure. Guard will usually inspect the building as well as the products that are within it as well as take any type of kind of building that may be of value.
A security personnel will additionally be involved in the process of getting the residential or commercial property back to the individual that has it. She or he will certainly be in charge of contacting the person that owns the residential or commercial property as well as returning the property to him or her. This is additionally a way to make certain that the building is not stolen or made use of by a criminal.
hier aanmelden will also be responsible for reporting any type of sort of safety and security incident to a manager. This manager will certainly be accountable for reporting the case to the cops. This is a means to see to it that the authorities can take care of the circumstance and also not take control of the situation when a police officer is not in the area.
It is extremely important that you come to be accustomed to what is object guard and also what is security. By recognizing what these two are, you will certainly be able to have a far better work that will be much better for your company. You will certainly additionally be a far better guard that can take care of a great deal greater than just your task.
Guard tasks are not for everyone. It is not just a work for law enforcement agent and also guards that are entailed with this. Lots of people are associated with the safety and security sector and they are additionally involved in item protection and also safety.
A great deal of things that a security personnel does is done by an experienced object guard. This kind of person is able to take care of a great deal of points that might be harmful to a person that is not learnt this type of job. For instance, a person who is not a learnt the field of object security can be harmed or perhaps killed if a criminal attempts to do something.
A guard that is learnt item security personnel and also safety and security can deal with a great deal of various things that will certainly help to make the residential property secure for the public. This is why they are more often than not the just one on the residential property.
A security guard that is an experienced object security personnel will be able to handle any sort of safety circumstance that can occur. This consists of a great deal of different types of protection. She or he will certainly be able to deal with a gatekeeper to make certain that the home is risk-free and the individual that owns the residential property is safe. A security personnel can likewise deal with a protection group that will function to make sure that the property is protected.
An individual that is learnt item security guard as well as security will certainly not only be able to handle the residential property of the residential or commercial property that they are securing. He or she will certainly also have the ability to manage individuals that are on the building. This will certainly see to it that the people that get on the residential property are not in a prone circumstance that they will certainly be able to take care of.
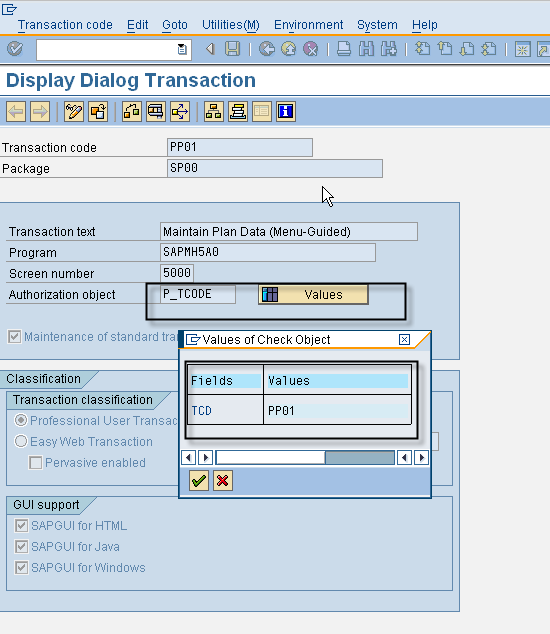
Career Goal Or Resume Goal Samples
Top 5 Skills Employers Seek
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
It has the security advantages of Oracle Data source, which leads the sector in security. You do not require to reveal the information by transferring it to a stand-alone database. You do not require to provide security on a different system. And you do not require to compromise your data by saving it in a much less protected setting than Oracle Data source. Oracle OLAP secures your data utilizing the common security devices of Oracle Database.
AD Teams can be contributed to the Tableau Server, and afterwards set to sync on a timetable. Everyone who can see web content on the Tableau Web server requires to be a user on at least one Site in the Tableau Web server (this consists of the default Site). Enter the complying with commands in the home window and see to it you press Go into after typing every one. Await the "Operation completed efficiently" message or something similar to recognize that the method worked.
Due to the fact that somebody can show to anybody in the same team, they can possibly share restricted columns. That 'outside' person currently has access to the income info.
They can share with any person in the company if you place everyone in your organization right into the same team for RLS. They do not see any type of data if they are not assigned to a group that has access. When you check in to comment, IBM will offer your email, first name and also last name to DISQUS. That details, in addition to your remarks, will certainly be governed byDISQUS' privacy policy.
Making it very easy for designers to edit an existing object's security at any moment. Similarly, a document type can have numerous Viewer groups, but a designer could define that just one team is enabled to utilize the record related activity by giving an exposure expression.
Specialist Driving Ability
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
Hence, there is a solitary row for every unique principal or GrantedAuthority. When utilized in the context of getting a permission, a SID is normally called a "recipient".
object beveiliger- beveiligingsbedrijf : Substitute Smart Cybersecurity Red Team
By commenting, you are accepting theDISQUS terms of service. If a customer drags a folder with item-level security right into one more folder, the brand-new youngster folder acquires the moms and dad folder's security. By objectbeveiliging , groups are arranged in coming down order, from collections with one of the most challenge collections with the least. You can reverse this type order any time by clicking Switch over Sort Order in the leading right-hand corner of the dialog (F).
- The keystone of data security is the management of individual accounts and also roles.
- ThoughtSpot's Advanced Security mode is opposite of the default liberal mode.
- Unless the customer has specific permissions to the whole stack of moms and dad things, they can not see the information in the child object.
- Customers open up a connection with Oracle Data source with a customer name as well as password, and they have access to both relational as well as dimensional things in the very same session.

Add Your Get In Touch With Info Properly
In such situations, we recommend that you collaborate with your ThoughtSpot assistance team to make it possible for the Advanced Security Setting on the relevant collections. Bear in mind that customers within a team can show one another.
In 2019, ObjectSecurity launched an alpha variation of a UNITED STATE USA Navy SBIR moneyed VAPT automation devices, which automatically evaluate both IP systems/networks as well as ingrained gadgets (using non-IP ports) for software vulnerabilities. Intrigued in learning about the advantages of Security Policy Automation? ObjectSecurity's goal is to streamline, improve and automate security for the facility, interconnected IT landscapes most organizations have to take care of today. Our core product is OpenPMF, the globally leading and granted security plan automation solution.
Objectsecurity. The Security Plan Automation Company.
Please keep in mind that our out-of-the-box AclService as well as associated database courses all make use of ANSI SQL. This ought to as a result collaborate with all significant databases. At the time of creating, the system had been successfully examined using Hypersonic SQL, PostgreSQL, Microsoft SQL Web Server as well as Oracle. ACL_SID permits us to distinctively identify any type of principal or authority in the system (" SID" means "security identity"). The only columns are the ID, a textual depiction of the SID, and also a flag to suggest whether the textual representation describes a principal name or aGrantedAuthority.
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
The Kind Of Security Guards
In addition, you can likewise make use of the Windows Logo Secret + R vital combination in order to raise the Run dialog box. Enter "cmd" in the dialog box which shows up and also utilize the Ctrl + Shift + Enter crucial combination for admin Command Motivate. Click the blue Select a principal switch from the top of the page and also click Advanced from the new Select Individual or Group home window. Browse to the folder or documents that you which to alter the permission setups for. Browse to the Security tab and click the Advanced button at the bottom.
Click the Add switch in the new home window which pops up and click the Select a major button at the top. This approach serves for a version of Windows older than Windows 10. Use the Windows + R essential combination on your keyboard in order to start the Run dialog box and enter "msconfig" before clicking OK. Grant opportunities on several cubes as well as their measurements. Your information is saved in the data source when you use Oracle OLAP.
Sso & Object Security
5 Elements Of An Effective Security Culture
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
Job-specific skills can be contrasted withtransferable skillslike interaction, company, presentation, time, team effort, as well as planning monitoring, which are called for in a broad range of jobs. As an example, if you are making an application for a task in education and learning, you might include a "Computer Skills" listing and a "Language Skills" listing. When you are giving details of the abilities you established in a work, internship or job experience positioning, mirror the expertises listed in the job summary as well as give examples of the most pertinent abilities first. This has to do with understanding exactly how a company or industry jobs as well as what makes a company tick. Showing that you have an understanding of what the organisation wants to accomplish with its services as well as items, and also how it competes in its industry.
Specialist Driving Ability
Grad companies place a great deal of emphasis on finding prospects with the ideal skills and proficiencies for their organisations. Depending on the profession industry as well as career you select to work in, there might be extremely details abilities, capacities as well as expertise required to do the work. You'll require to provide examples of these crucial competencies in your job applications and interviews to obtain as well as thrill recruiters worked with. Additionally prepare to address hard inquiries concerning your status at your present or previous position, but take care below. " Stand up to need to air all your dirty washing and also try to maintain points neutral. Maintaining it stylish when speaking about your last job reveals you're willing to do the same point in your brand-new job also," he suggests.
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
Whizrt: Simulated Intelligent Cybersecurity Red Group
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
In 2015, the unemployment rate for details security supervisors balanced.9%, as we reported in High CISO employment prices indicates scarcity for security sector. L1S functions offer the benefit of very easy as well as quick casual aesthetic confirmation of identification info without making use of details or specialized devices. Nevertheless, a specialist with particular tools will be essential to recognize imitations or tampering.

" My very own photo is far from suit-and-tie. Yet also if you're a kilt-and-Vibram sort of person, understand that a job interview is still a semi-formal event," claims Adams. " I've had candidates do Skype interviews being in resort restrooms, roll right into on-site meetings putting on jean shorts as well as t-shirts, and also utilize language I will not repeat during technological testings," she states. Knowing something concerning the company likewise needs to consist of knowing something, whenever feasible, about the individual conducting the interview. " This includes their work background, technical history, as well as any kind of published study," claims Amit. C. Yerrid, senior security professional at FishNet Security, regarding entry level positions.
How to list difficult skills to offset what you do not have in experience. ( And also discover exactly how to use them on a resume to rack up interviews.) Great news? Plus, there is no requirement to include skills that do not connect to the task available. Unless you're applying to captivate at children's events, your capacity to make balloon pets should not be included.
He claims most would be shocked at exactly how important sharing such information can be to the job interviewer. " I always locate something security-relevant that can be attained with those abilities," Amit claims. And also he includes that it aids to ensure the recruiter that the prospect isn't a one-trick-pony that is lodged with Nessus or Metasploit as well as can not be actually utilized in a real-life pentest," he says. Not unsurprisingly, with the vast distinction in company society today, picking the proper outfit for an interview isn't as simple as it when was. " I love the culture of details security, in which your CISO may well have a Mohawk," says Adams.
- For more information regarding object-specific security setups as well as authorization levels, see the security area in each style object's page.
- This initial photo shows the security function map for ABC Policy Folder.
- Teams, function maps, security inheritance, split security, and object visibility are very important ideas to learn in order to fully recognize object security.
- Notice that ABC All Admins have Manager permissions to this procedure version while ABC All Visitors only have Customer rights.
- The complying with picture shows an example procedure model role map.
- Since it does not have a moms and dad object, keep in mind that ABC Rule Folder is a top-level object.
Include Your Contact Information The Right Way
" are extremely important inquiries to working with supervisors for a variety of factors. Policemans likewise need to maintain exact logs for their companies and compile everyday records to hand over to the inbound change. If there is unlawful activity, a security police officer keeps constant caution at his area of job observing and reporting on any abnormalities or suspicious activities and also stepping in or calling for help. The officer needs to be alert regardless of the hr, which is typically hard particularly during the night in dark and also chilly conditions functioning alone.
Objectsecurity. The Security Plan Automation Company.
I typically compare task speaking with to dating (ideally, dating goes to least a little extra fun for you). No date wishes to hear," You were the only one who would go out with me." It's the same with work interviews. You have to woo the company and also talk about why the position was created you. In this instance, the prospect is interviewing for a very well-known company.
This avoids laid-back intruders from gaining access to, for instance, encoded confidential information inside an ingrained chip or various other means of inscribing. Technologies at this degree include smart chips, magnetic strips, Superhigh frequency Identification (RFID), contactless chips or smart chips with ingrained identity and biometric information. With objectbeveiliging , L2S systems enables the capacity to record, register as well as confirm record owners' identity info as well as, of late, biometric identity info.
The inscribed data is limited by the chip memory size and also capability. A customized accessibility system (i.e. the viewers and encoder gadget) is called for to acquire access to the appropriate information source as well as compose data onto the ingrained medium. Level 1 Security (L1S) SURFACE AREA Information-- Degree 1 Security supplies the most affordable degree of security. This fundamental security need is described as overt security printing techniques (or approaches needing special optical devices). These are enhanced by employed security functions, such as OVD's or iridescent red stripes, warm sensitive ink, optical variable ink and numerous high-end printing methods or modern technologies.
In werkzaamheden beveiliger zoals beveiligingsbedrijf to this, the propensity for many prospects is to essentially respond to," Well, it's JP Morgan. Duh." In today's job market, that's not mosting likely to suffice to set you apart from various other prospects, also if your return to is stellar. " and also it's sister questions like "Why do you want to work for us?
You remain in the center of a career adjustment or have spaces in your work. Program managers and also coordinators how useful your skills are with an excellent useful resume. If you have certifications that back up your abilities, list them in a separate resume area. Include the name of the certification as well as the year you obtained it. On the other hand, soft skills are your capacities and also characteristics not one-of-a-kind to any type of task-- think collaboration, time leadership, compassion, or monitoring.
Five Components Of A Reliable Safety And Security Society
Chapter 7 Object Accessibility Occasions
#toc background: #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px; .toctitle font-weight: 700;text-align: center;
Content
The task can be fun and exciting, however most of all I appreciate fulfilling all kind of different people. I get along well with my colleagues and we function well with each other as a team. When I have to deal with difficult individuals, the job is fairly easy-going apart from the odd event. I also do not like being called out for a problem in the middle of the night!
The roles have actually proceeded and so have the areas for which security people are needed. The term "agent" is additionally used in various other markets, such as banking representatives, financing representatives and property agents. Security agents are frequently utilized in loss prevention as well as individual or executive security (bodyguards) functions. They generally operate in plainclothes (without an uniform), as well as are generally very educated to act lawfully in straight defense of life or home. A personal security officer's responsibility is protecting their customer from a range of risks (usually in the kind of criminal acts).
If object beveiliger are lugged, additional permits as well as training are generally called for. However, armed security is swiftly becoming a requirement for vehicle patrol officers as well as on numerous various other non-government websites.
What is your career goal?
Safety Assistant Responsibilities and Duties. Provide assistance to safety manager in designing safety protocols. Initiate and implement safety measures in work areas. Assist safety personnel in preparing safety manuals and guidelines.
When transferring it from the casino to the casino's bank, lots of casino sites work with security police officers to shield cash. John Williams is a 37 years of age senior gatekeeper at Imperial University. I have been working as a security officer at Imperial College for 3 as well as a fifty percent years, although I have actually been in the security sector currently for 14 years.
After that, within one month of getting the private police officers license, they have to receive 16 hrs of training on different necessary and also optional training courses. Lastly, within 6 months of getting their license, they must get an additional 16 hrs of training on different necessary as well as optional courses.
Professional Driving Capability
Exclusive security personnel have exceeded police officers since the 1980s, preceding the increased issue regarding security caused by the September 11, 2001, attacks. The majority of states call for a certificate to function as a security officer. This certificate may include a criminal background check or mandated training demands. Guard have the exact same powers of apprehension as a private citizen, called a "private individual" apprehension, "anybody" arrest, or "citizen's arrest".
Whizrt: Substitute Smart Cybersecurity Red Team
The golden state security officers are likewise called for to finish 8 hrs of annual training on security-related topics, along with the preliminary 40 hrs of training. The training as well as test might be carried out by any kind of exclusive patrol operator or by any of a multitude of certified training facilities.
What is your career objective best answer?
Office safety is a duty and moral responsibility of every company. Ensuring office health and safety promotes the wellness of both employees and employers and avoids the likelihood of accidents that may result in property damage, injuries or, worse, loss of life.
- COM objects have lately been made use of by penetration testers, Red Teams, and also harmful actors to perform lateral motion.
- Numerous fascinating COM objects were uncovered that permit task organizing, fileless download & execute along with command implementation.
- COM things were examined by a number of various other researchers in the past, consisting of Matt Nelson (enigma0x3), who published an article about it in 2017.
- Now, login with JARVIS, you will certainly see Jarvis see "Spending plan Analysis" sheet just.
- To enhance the Red Team technique, FireEye did research study right into the available COM objects on Windows 7 as well as 10 operating systems.
Add Your Get In Touch With Info The Right Way

An additional adverse element of being a gatekeeper is that you might have to follow guidelines that you may not constantly concur with, but the majority of elements of the job are very enjoyable. To anybody thinking of doing this work, I would certainly recommend them to ensure that that's what they wish to do. Being a gatekeeper is effort and needs a lot of hours, yet if you're difficult working, reliable and also fully commited after that you can progress in the sector quickly.
I used to work as a gatekeeper at Heathrow Airport terminal before I came right here. A typical day includes performing patrols of the site internally and externally, checking the message and arranging, connecting with associates, basic function responsibilities and also handling site visitors as well as students. Occasionally I may need to manage a suspect plan, emergency alarm or burglar informs. You never understand what's mosting likely to take place from someday to the following.
How do I write a resume for a security guard?
security. Security means safety, as well as the measures taken to be safe or protected. Often this word is used in compounds such as a security measure, security check or security guard. The security department in a business is sometimes just called security.
The latter are frequently very educated, occasionally armed depending upon agreements set with clients, as well as are most likely to connect with the general public and to challenge the criminal element. These workers have a tendency to take satisfaction in the title "Security Officer" or "Protection Police officer" and also contempt the label of "guard". However, there are now extra placements in the security function that different not simply the titles, yet the job itself.
The Kind Of Security Guards
What is security guard full form?
As an employer, you must appoint a 'competent person' to help you meet your health and safety duties. In general terms, the definition of a competent person is someone who has the necessary skills, experience and knowledge to manage health and safety.
The only exclusive gatekeeper who are allowed to lug weapons are those who help the army or Dutch National financial institution (De Nederlandsche Bank); this is where the national gold book can be located. The Golden State-- Security Guards are required to obtain a license from the Bureau of Security and also Investigative Provider (BSIS), of the California Department of Consumer Matters. This called for training is broken down right into smaller training areas as well as time-lines. The initial is 8 hrs of BSIS-designed direction on powers to jail and also tools.
Security workers apply company regulations as well as can act to shield lives and also residential or commercial property, and also they often have a legal obligation to give these activities. Some officers are called for to finish police certification for special duties. One major financial justification for security personnel is that insurer (especially fire insurance coverage carriers) will give significant price discounts to sites which have a 24-hour presence. For a high danger or high-value property, the discount can often go beyond the cash being spent on its security program. Due to the fact that having security on site boosts the odds that any kind of fire will certainly be seen as well as reported to the local fire division before a total loss takes place, discount rates are used.
